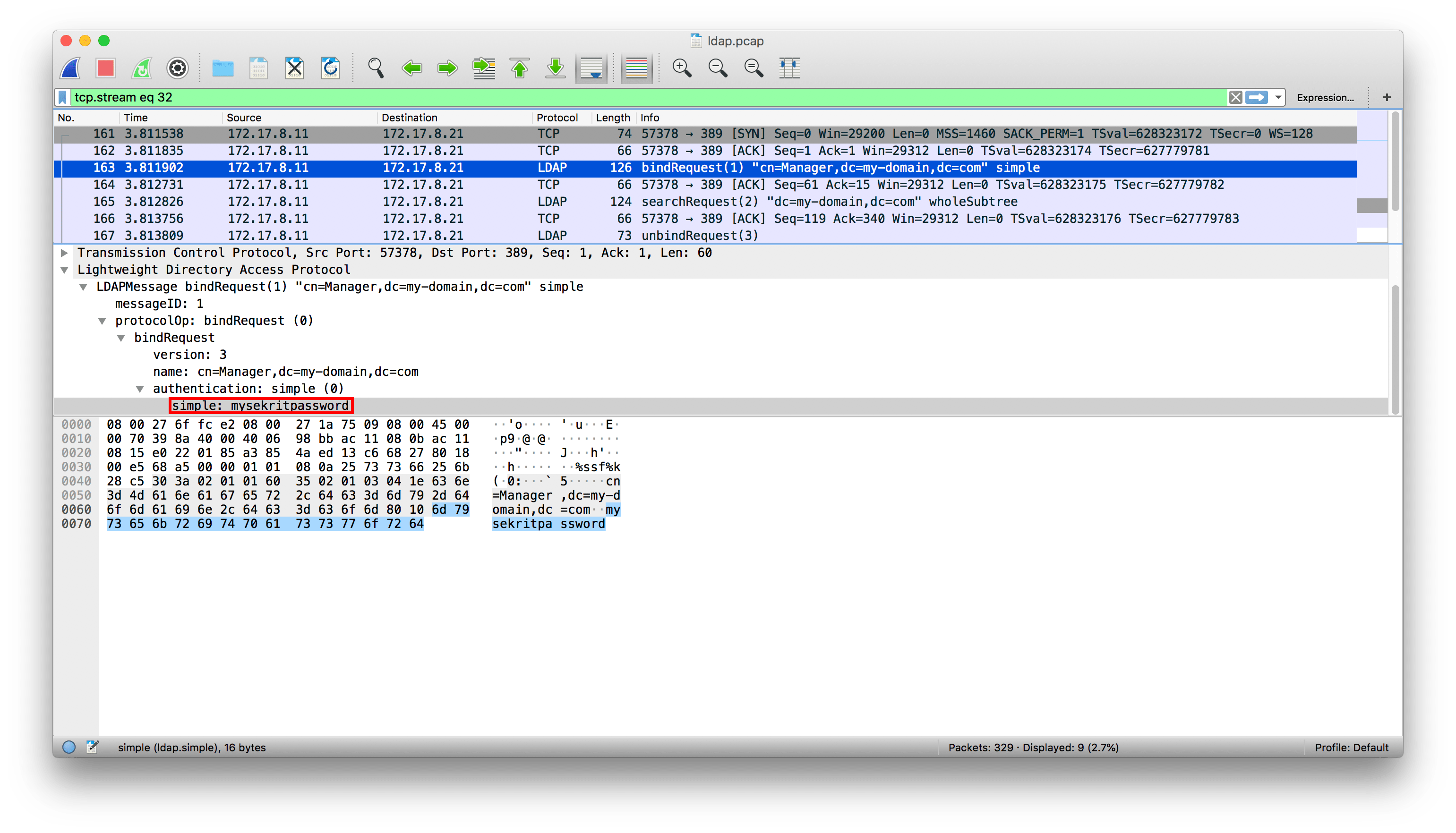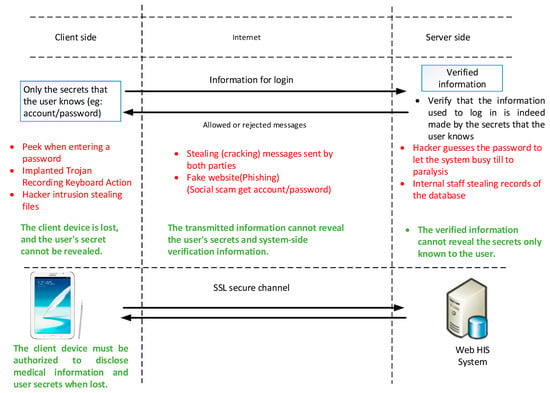
Sensors | Free Full-Text | Study of Out-Of-Hospital Access to HIS System: A Security Perspective | HTML

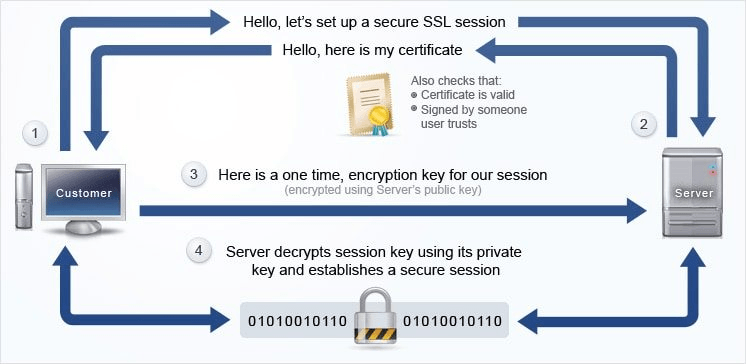
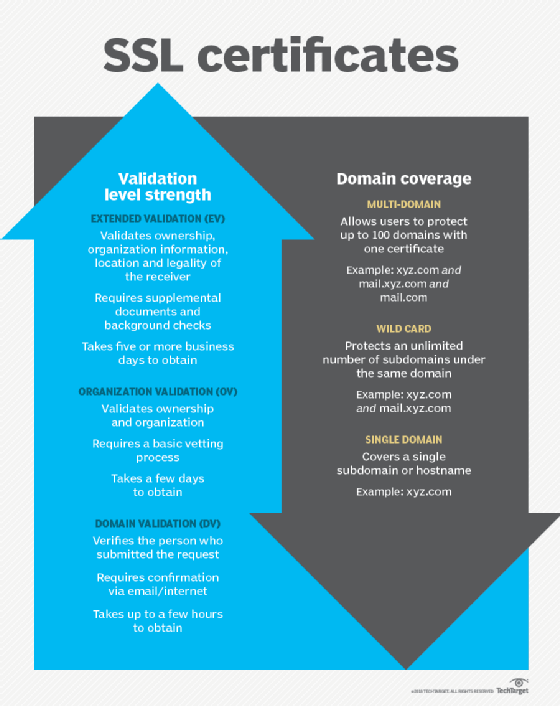
What Is the Difference Between SSL/TLS vs. SSH, HTTP vs. HTTPS, and FTP vs. SFTP? | phpGrid - PHP Datagrid

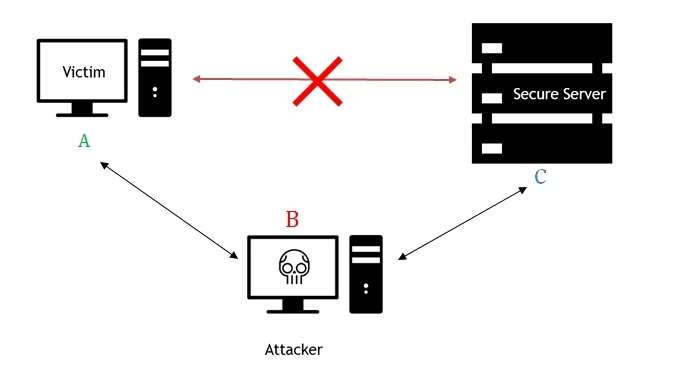
How Journalists Are Coping with a Heightened Surveillance Threat - Global Investigative Journalism Network
![Cisco PCI Solution for Retail 2.0 Design and Implementation Guide - Component Assessment [Design Zone for Retail] - Cisco Cisco PCI Solution for Retail 2.0 Design and Implementation Guide - Component Assessment [Design Zone for Retail] - Cisco](https://www.cisco.com/c/dam/en/us/td/docs/solutions/Verticals/PCI_Retail/ch5_PCI.fm/_jcr_content/renditions/ch5_PCI-005.jpg)
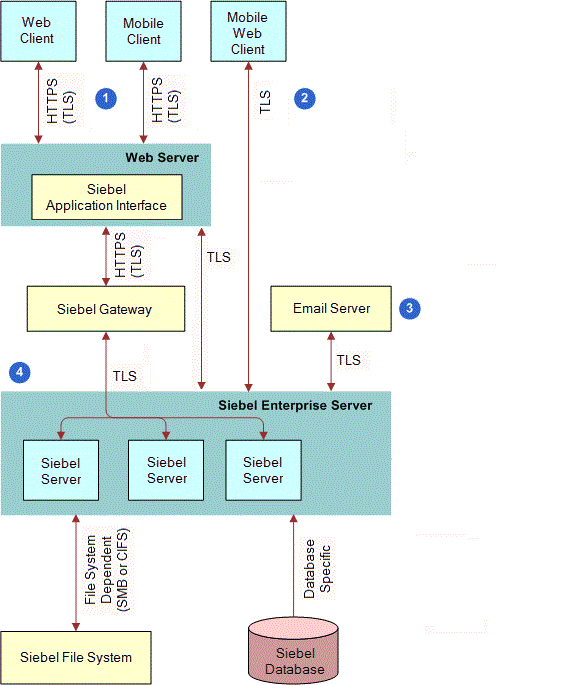
Cisco PCI Solution for Retail 2.0 Design and Implementation Guide - Component Assessment [Design Zone for Retail] - Cisco

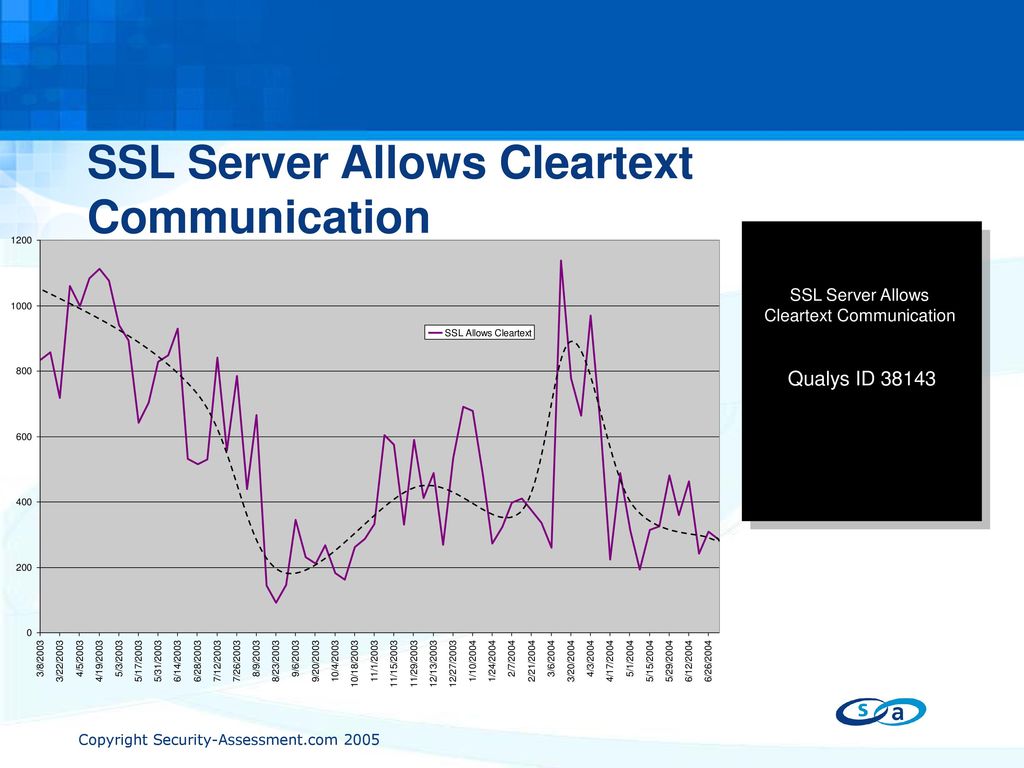
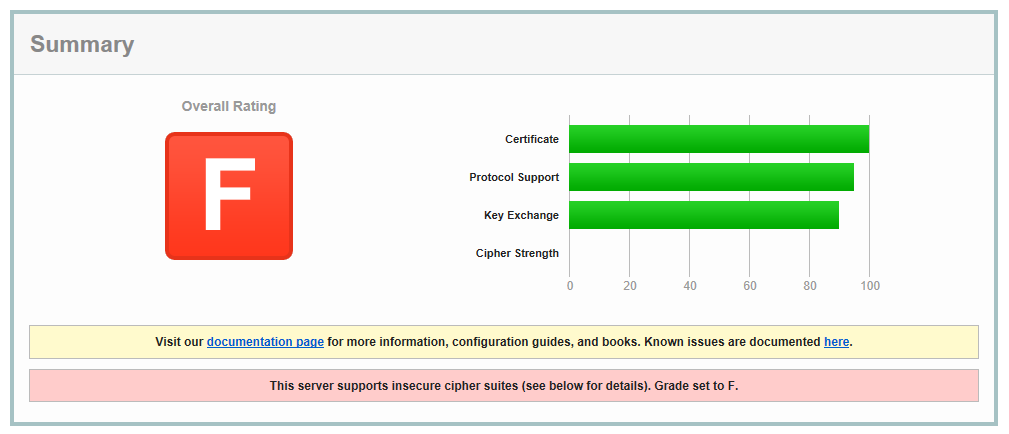
The most recent SSL security attacks: origins, implementation, evaluation, and suggested countermeasures - El‐Hajj - 2012 - Security and Communication Networks - Wiley Online Library
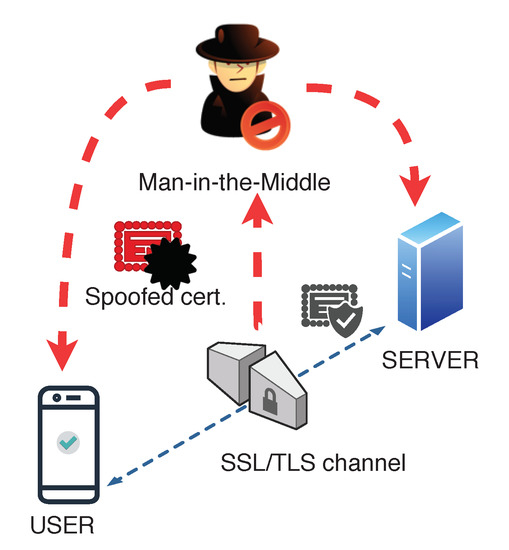
.png?width=1941&name=Blog%20%2341-01%20(1).png)
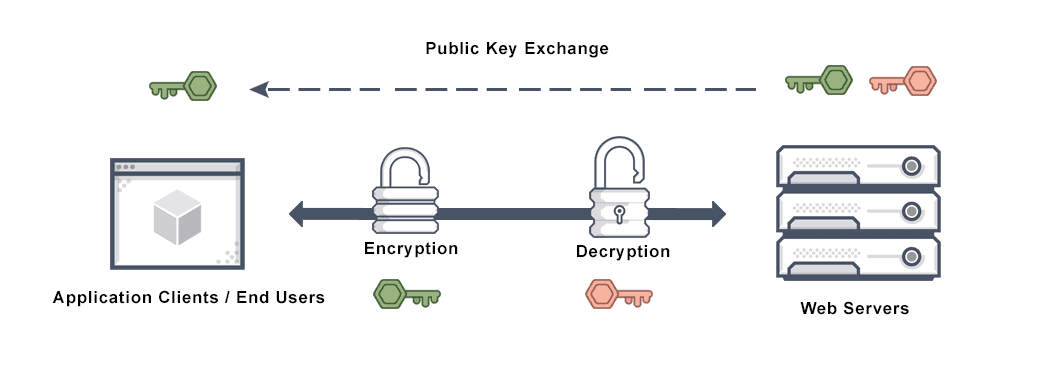
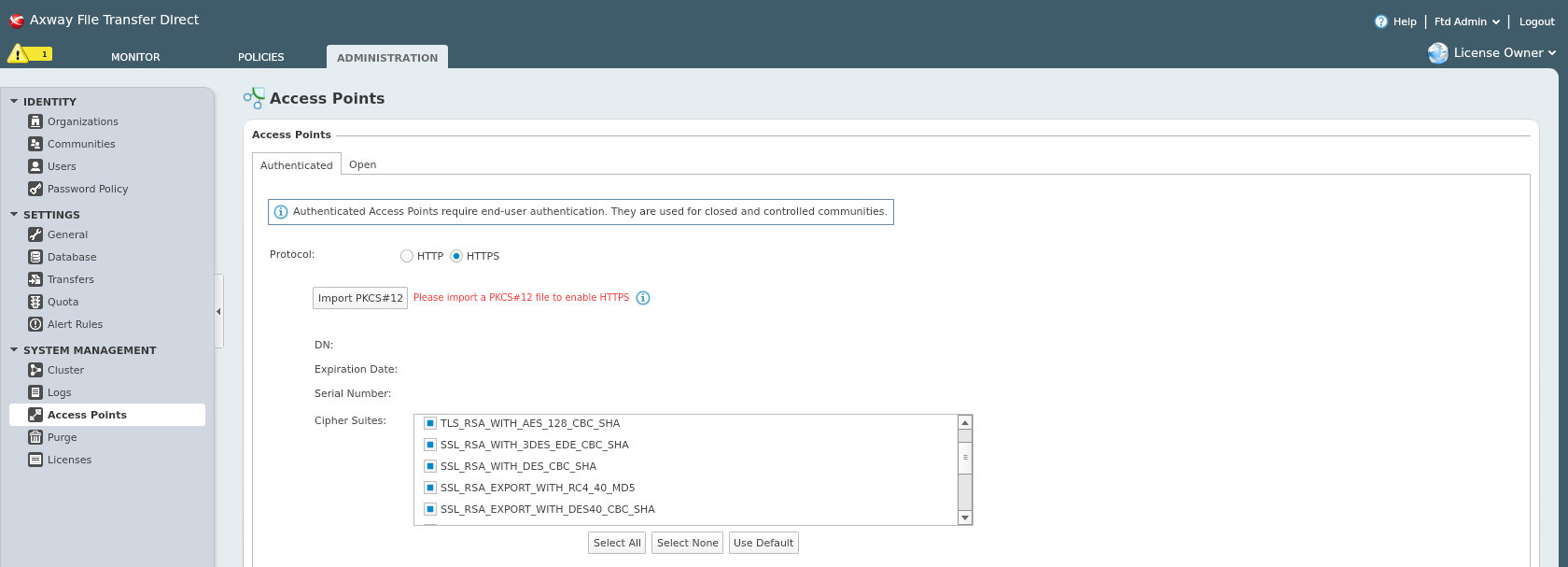
![SSL & TLS HTTPS Testing [Definitive Guide] - Aptive SSL & TLS HTTPS Testing [Definitive Guide] - Aptive](https://www.aptive.co.uk/wp-content/uploads/2017/01/testssl.sh-enum-ciphers-per-ssl-tls-protocol.png)